Common Concerns When Implementing IoT (And How to Respond)

How to Convince Your CEO to Invest in IoT (3/3)
This is the part 3 of our “How to convince your CEO to invest in IoT” blog series. Previously in part 1, we demonstrated some organizational and institutionally biasis against IoT. Then, in part 2, we explained the fundamental components of IoT and the benefits of implementation. Lastly, in this part 3, we will conclude with some common concerns with answers worth presenting to leadership.
Common Concerns and How to Respond
Senior leaders have vast experience and time-tested decision-making skills which has trained them to anticipate risk. No need to test their abilities, but instead better to support their decision making skills with an innovative possibility. Here are some of the most common concerns about IoT and how to respond:
How To Make Sure Your Company’s IoT Projects Are Secure?
Ecliplse sponsored a survey in 2016 to better understand how developers are building IoT solutions. This survey found that nearly 50% of respondents chose security as the main concern. So, what is data security anyway?
Data security consists in privacy, integrity and availability.
Data privacy consists is the ability for an organization to manage information and determine which information is sensitive and should be restricted. Data encryption is a common way businesses and individuals ensure privacy and consists of transforming data to disguise it from unauthorized individuals.
Data integrity represents an accuracy and consistency in making data available, reliable, and useful. For instance, data integrity is achieved when an IoT platform provider ensures constant data readings with optimal connectivity and hardware for a given environment.
All the while, data availability refers to the capacity to keeping a system operating. In IoT, for instance, availability is understood to be the capacity to access a backup data source when an unexpected downtime occurs.
Companies can make sure to keep IoT data private, honest, and available by using recommended best practices and adhering to standards within each of the IoT components: devices, connectivity and IoT platform.
Here are some common practices recommended to any IoT developer looking to better understand security:
- HTTPS access: is a security protocol used to protect a website from unwanted intruders. Fraudsters have been known to use web resources such as the HTML or commands in order to confuse users into inadvertently providing personal information or installing malware when visiting websites
- Token based authentication for device APIs: the traditional server-based authentication method is not recommended for IoT devices. Such method required the server to store the access information (like a username and password) and then grant access to the client providing those credentials. This poses a security risk in case a third party gained access to those credentials. Yes, you could just change your password, but then you would have to change the password hardcoded in thousands of devices deployed. To overcome this, API designers came up with the token based authentication, which follows this logic:
- The client (a device) requests access with Username / Password or an API Key
- The Application validates credentials and provides a token to the client
- Client stores that token and sends it along with every request
- Server verifies token and accepts the requests
This way, if a communication is compromised, then the token can be revoked in the server side and the devices would just request a new token in the next request. No need to change the firmware of thousands of remote devices.
- Access control for customers and users: app admins can determine the levels of access of each new user within an application. Admins can even specify if they want users to edit, create, or only visualize certain information, dashboards, or widgets.
- 2X data replication: if you lose a devices data readings for a particular reason, you should always have the peace of mind that these readings are being stored somewhere in parallel.
- Encrypted transport: for ensuring data privacy, the data sent from devices to the cloud should encrypted so it cannot be easily understood by unauthorized individuals.
Is IoT Financially Attainable For Your Company?
One of the barriers to adopt new technologies are upfront costs. However, according to Goldman Sachs, numerous triggers are turning the IoT from a futuristic buzzword into a reality. The cost of sensors, processing power, and bandwidth to connect devices has dropped low enough to spur widespread deployment:
- Sensors costs have dropped to average 60 cents from $1.30 in the past 10 years.
- Bandwidth costs have dropped by nearly a factor of 40X in the past 10 years.
- Processing costs have dropped by nearly 60X in the past 10 years.
So even if your IoT solution appears to have a higher cost than the value it can generate in the long term, you should still do the project; chances are the prices will drop and you will become the first player in your industry to have the solution that your competitors saw as financially impossible.
Is IoT Just Hype?
Different thought leaders have shown special dedication and interest around the Internet of Things.
Goldman Sachs Global Investment Research proposed these five verticals for IoT adoption. The earliest aporters (which we are already seeing) are wearables, cars, and homes with cities and industrial applications following closely behind.
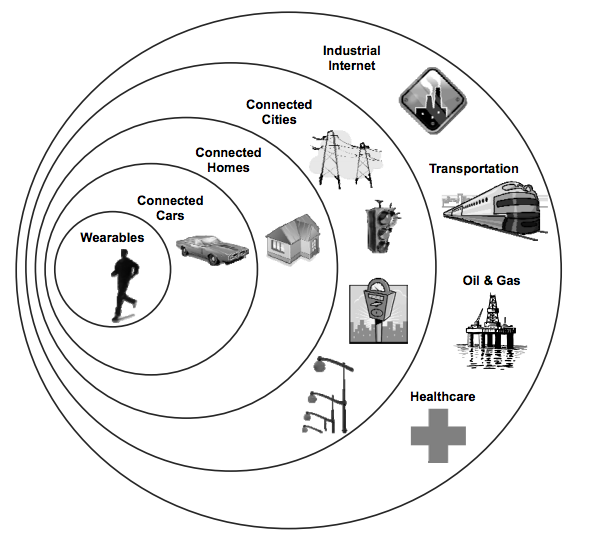 Source:Goldman Sachs Global Investment Research.
Source:Goldman Sachs Global Investment Research.
Goldman Sachs released a report called “The Internet of Things: Making sense of the next mega-trend,” suggesting IoT will be the third wave of Internet, which may be the biggest. The frist two waves being fixed internet during 1990s and mobile internet throughout the 2000s.
The World Economic Forum features the Internet of Things as one of the technologies that will shape the 4th Industrial Revolution in the Future of Jobs Report (2016), and even dedicated a single research on the Industrial Internet of Things in collaboration with Accenture.
Tech companies such as Google, IBM, Amazon, Samsung and Intel have developed their own Internet of Things platforms to leverage new applications.
Nations are paying attention to the Internet of Things too. The French government is deploying a Lora network to ensure entire internet connectivity throughout France. Meanwhile, Germany coined the term Industrie 4.0 in an effort to move industry to the 4th Industrial Revolution.
How Does The IoT Fit Into Your Industry?
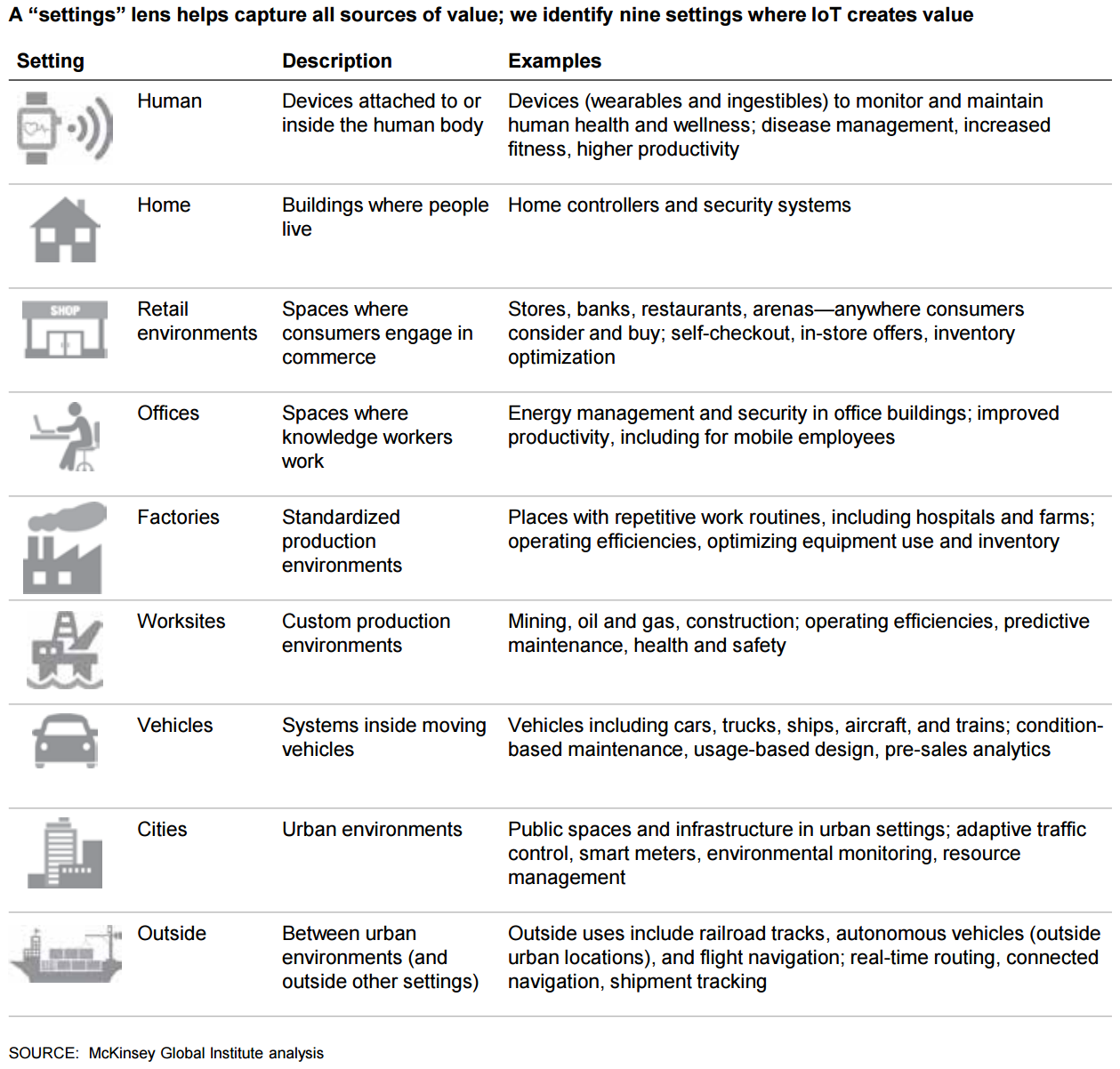
Mckinsey released the Mapping The Value Beyond The Hype study in order to know the economic value of IoT across industries. The findings of McKinsey suggest that IoT has the power to impact directly or indirectly every single industry. Where do you fit in IoT?
Next Steps to Starting Your Own Projec
If you were successful in conveying the value of the Internet of Things to your organization, we welcome you to take at Ubidots IoT Application Development and Deployment Platform to the next steps in your prototyping, testing, and scaling:
- Create a free Ubidots account: start prototyping and building IoT projects using Ubidots.
We’re happy to help you in your IoT journey, reach the Ubidots team at sales@ubidots.com with any additional questions or consultation requests.